
In this course, students will be able to understand the principles and different tools of digital forensics. Some of the topics included in the unit are-
Threats that modern network infrastructure face in terms of security
Implementation of forensic analysis
How to collect forensic material for expert analysis
How to overcome legal, ethical and professional problems in the field of Information security
We at Quick Assignment Hub offer exclusive Melbourne Institute of Technology assignment Help for this course.
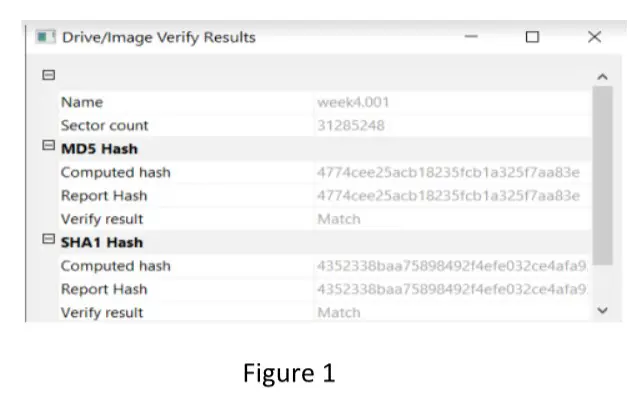
a) Explain how Hash Values can be used to validate data in digital forensics given in Figure 1. (5 Marks)
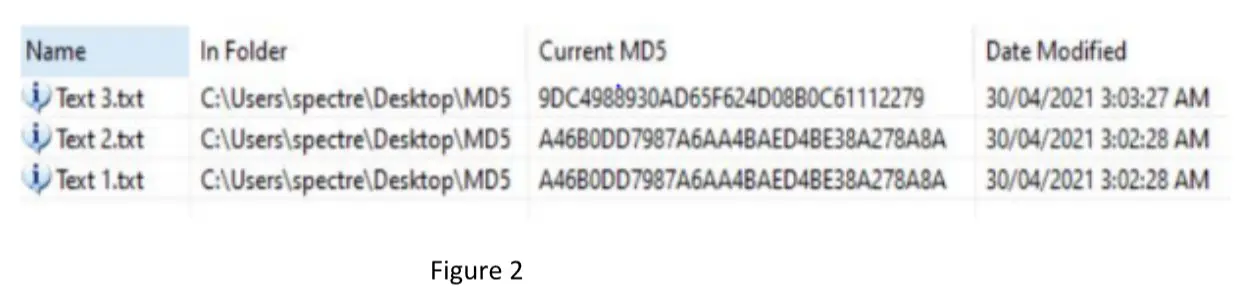
b) Examine and analyze the MD5 results given in Figure 2. (5 Marks)
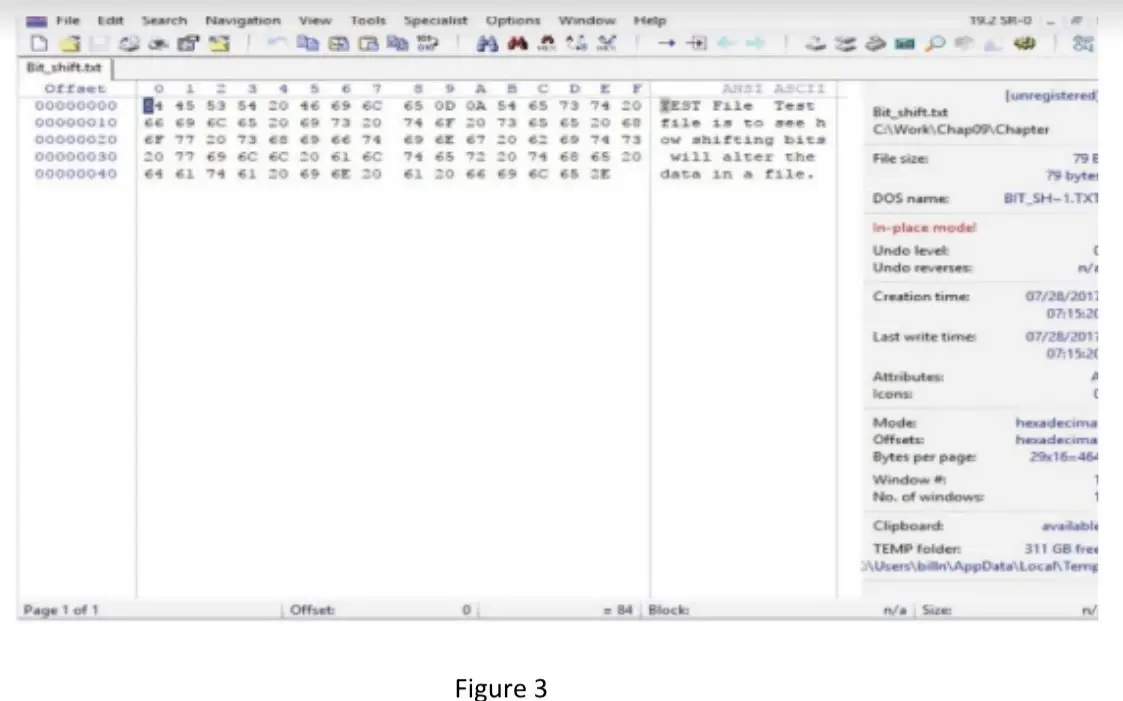
c) Explain the data hiding technique(s), used in Figure 3. (5 Marks)
Ryan is a hacker who plans to exploit victims by uploading a malicious webpage in the cloud. He uses a vulnerability to exploit the cloud presence of XYZ Coffee, a legitimate company. From there, he installs malware that inserts a malicious payload into web pages displayed, social media, and hides his malicious activity from the anti-virus. He then redirects victims to the website, which infects them with malware. In addition, the hacker used anti-forensics tools. Users complain to the legitimate company that they are being infected, so the company seeks to fix the problem and investigate the crime.
Answer the following questions based on this scenario.
a) Provide a list of potential digital evidence and media that the investigator is going to seize for possible forensic examination in this case study. How would you gain access to this evidence? (2+3= 5 Marks)
b) Explain two acquisition methods that you should use in this situation. (5 Marks)
c) Describe significant challenges with cloud forensics, including forensic acquisition and evidence preservation. (5 Marks)
d) Explain what “anti-forensics” is, and provide detail on some anti-forensics tactics that could be used in this case study. (2+3=5 marks)
e) How should you proceed if the suspect's computer is running? (5 marks)
A new start-up SME (small-medium enterprise) based in Melbourne with an E-government model has recently begun to notice anomalies in its accounting and product records. It has undertaken an initial check of system log files, and there are many suspicious entries and IP addresses with a large amount of data being sent outside the company firewall. They have also recently received a number of customer complaints saying that there is often a strange message displayed during order processing, and they are often redirected to a payment page that does not look legitimate. Address the following questions while preparing your report as a digital forensics investigator.
a) Why are network router logs important during an email investigation? (5 Marks)
b) Explore the techniques and tools that can be used in this situation. (5 Marks)
c) Describe significant challenges with network forensics in this network, including forensic acquisition and evidence preservation. (5 Marks)
d) Identify and explain three types of log files you should examine after a network intrusion. (5 Marks)
e) When are live acquisitions useful? (5 Marks)
You are investigating a cybersecurity crime that needs mobile forensic analysis. You contacted the company's IT department and they gave you data from all employees' mobiles. The data is more than 100 TB and the time for investigation is not long enough that you can analyze all data. How would you address the following questions while preparing your report as a digital forensics investigator?
a) Discuss and analyze how to perform a full forensics investigation and discuss the steps required in acquiring the evidence in consideration of legal and ethical standards. At each step explain which tool you will use and if you would like to have more information regarding any employee from the company. (5 Marks)
b) Discuss the general procedure to access the content on this mobile phone SIM card. (5 Marks)
c) Explain the considerations you should have when deciding what data-acquisition method to use for your investigation. (5 Marks)
d) Discuss the obstacles that you can expect to encounter when acquiring evidence and your plan to mitigate them. (5 Marks)
e) Explain two acquisition methods that you should use in this situation and explain how do you validate your findings. (2.5+2.5= 5 Marks)